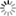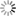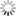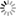Technical aspects of the OpenSecurity Project
After collecting and evaluating different techniques and approaches to Security by Isolation, the OpenSecurity team focused on designing a concrete solution for two different user scenarios that were prioritised by the project stakeholders: the transfer of data to and from mass storage devices and secure Internet browsing.
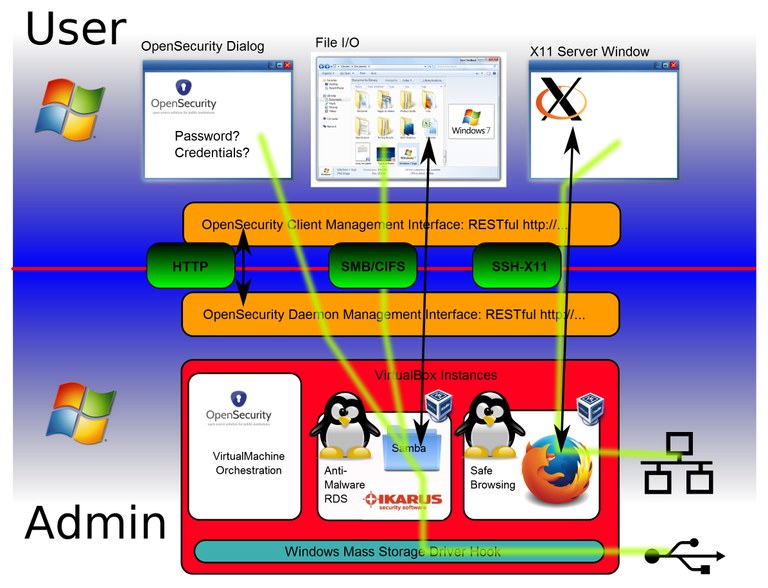
The work so far has resulted in a set of isolated core components interacting together to orchestrate dedicated virtual machines. The OpenSecurity components created in this process share well-defined open interfaces: RESTful API, CIFS and SSH. These protocols cleanly separate the different components of the OpenSecurity solution space, thus allowing the upgrade or even the complete exchange of these components without disrupting the concept and benefit of the whole system.
The central component of the OpenSecurity design is the OpenSecurity Management daemon, which starts and stops disposable virtual machines. These machines are instantiated templates which are created from the dedicated OpenSecurity Linux distribution derived from Debian 7.2. Other components take care of user interaction, device driver overlays, and embedding access from and to the virtual machines with respect to the current user session.
The team presented a live proof-of-concept in December, which demonstrated independent Virtual Box machines handling USB mass storage device actions like virus scanning and/or encryption, as well as a tight integration of an Internet Browsing application run inside a virtual machine but shown natively on a Windows 7 user session.
The on-going implementation work is now directed towards making the system stable, performant and flexible. Though the software components written in this context are rather small and the interfaces are all widely known and understood, the complexity stems from the fact that messages often do cross operating system boundaries with impact at very low level system functionalities. This situation plus the special characteristics and divergences of partly closed-source operating systems behaviours - even if coined "standard" - makes this a demanding and sophisticated endeavour.
Finally installation challenges must also be addressed in order to support both simple single-user one-click download setup-files as well as a full blown rollout on to thousands machines directed by a central IT department. As the OpenSecurity integration also relies on a range of well-developed and open source third-party software, version management is yet another complex task of its own to be tackled next.
Document Actions